Alternative title: why my mini0806 was crashing and stopped working after a light drop.
One of the differences between mini0805 and mini0806 is this heat sink:

It is a bitch to remove, so I gently coerced it with a blade:

After some time of gentle pushing and heating it managed to peel off:

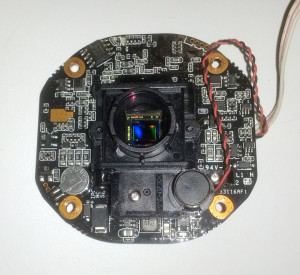
Revealing Samsung ram chip and Ambarella A7LA50 SoC:

Here is why it was not working after slight drop (and crashing before that):

Pulled out pads! Note that the blade I used to remove would cause other side of pads missing if I applied too much pressure.
My theory is following: the heat sink that bridges RAM and SoC is causing stress on these chips. Mostly because it is glued and not mechanically pressed against the chips. This is a very silly design flaw, if for example, only SoC would have the heat sink (like found on IP cameras) then there would not be any stresses. I don’t think RAM needs heat sinking on those things.
I am tempted to take dremel to my other mini and split the heat sink in two…