ILDVR INC-MH40D06
Attention: before you read all this, see this post!
A 4MP dome IP camera (this particular has 2.8mm lens) ordered from ildvr.com, somewhat unknown company between western IP camera enthusiasts (although it is known in Russian circles). I have stumbled up when researching new cameras on some Russian website.
Made an enquiry on ildvr.com expecting to have usual “go away” response (as in: “contact our useless resellers, that will not sell you anyway”). To my surprise I got a very quick reply with all my questioned answered.
The retail price of this camera is around $100USD (they charge extra for their windows software, in which I was not interested).
From hardware perspective this camera is similar to Dahua IPC-HDBW4300E.
It has metal construction with plastic dome. Biggest difference is that the Dahua has PoE circuit on the base, while ILDVR has it on the camera body.
The camera came in a cubic box which contained another box padded by thin layer of foam. One issue with packaging I had is that the bag containing the mounting screws was not sealed properly and spilled the screws. One of the screws managed to leave a scratch on the dome. This scratch is not a huge issue is that it is unlikely it will ever be in field of view.
The warranty sticker is a nice touch:

The ILDVR letters are bunch of stickers (I will probably remove them as they are a bit tacky):

Second warranty sticker on camera itself:

Note the string preventing the dome from falling. The screws are also captive and of torx type (a bit nicer than usual hex screws).

A close up of the scratch (nothing to really worry about):

The box contained a Torx “L” wrench, template, mounting screws/dowels and ethernet jack seal kit.
Note: there was no CD (normally containing crappy windows software) or manual.
An interesting feature is the ethernet status LEDs on the connector:

The cable itself is about 40cm long.
Technical details
Most of this stuff I discovered poking around while waiting for technical details from ILDVR.
I will fill in once I have more details.
With no help from ILDVR I managed to get shell on it.
ARMv7 Processor rev 5 (v7l)
128MB RAM
16MB Flash (MX25L128XX)
/proc/cpuinfo
Processor : ARMv7 Processor rev 5 (v7l)
BogoMIPS : 1196.85
Features : swp half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xc07
CPU revision : 5
Hardware : hi3516a
Revision : 0000
Serial : 0000000000000000free -m
total used free shared buffers
Mem: 121 64 57 0 0
-/+ buffers: 64 57
Swap: 0 0 0load hovers around 3 (less than Dahua and Hikvision).
uname -a
Linux ipc 3.4.35 #5 Fri May 8 10:31:07 CST 2015 armv7l GNU/Linuxdf -h
Filesystem Size Used Available Use% Mounted on
/dev/root 2.0M 2.0M 0 100% /
tmpfs 30.0M 19.9M 10.1M 66% /dev
tmpfs 30.0M 19.9M 10.1M 66% /tmp
tmpfs 30.0M 19.9M 10.1M 66% /dev
tmpfs 30.0M 19.9M 10.1M 66% /var
tmpfs 30.0M 19.9M 10.1M 66% /tmp
tmpfs 30.0M 19.9M 10.1M 66% /dev
tmpfs 30.0M 19.9M 10.1M 66% /var
/dev/mtdblock3 11.0M 8.5M 2.5M 77% /mnt/flash
tmpfs 30.0M 19.9M 10.1M 66% /mnt/flash/Server
tmpfs 30.0M 19.9M 10.1M 66% /usr/lib
tmpfs 30.0M 19.9M 10.1M 66% /etc
tmpfs 30.0M 19.9M 10.1M 66% /rootcat /mnt/flash/productinfo/deviceid.txt
DEVICEID V6202IR-OV4689I found actual manufacturer of the board:
http://www.hankvision.com/chanpin/wangluomozu/512.html
In case link goes away here is the screenshot:

They claim it is Hi3516D chipset.
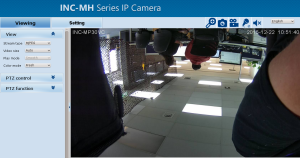
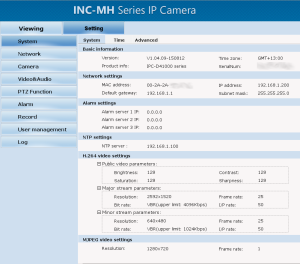
The webUI.
Default username and password is admin.
I was hoping for a more modern interface, the one without ActiveX/Windows only crap…
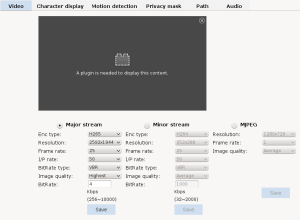
As usual the viewer is useless without ActiveX plugin, even if mjpeg is selected there is a bug where it only shows two frames.
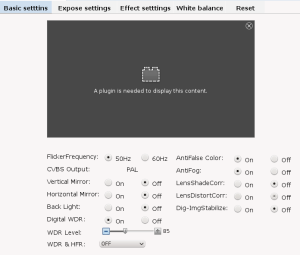
The Video and Camera settings are useless again due lack of plugin.
This webUI is on par on crappiness with Hikvision and Dahua.
One day we will have platform independent HTML5 interface… I hope.
MJPEG stream preview is a bit buggy (not really visible here):
The most important feature that is missing is Telnet/SSH control (I would rather turn off Telnet). The telnet is on all the time (I have enquired about telnet access).
There is also no control regarding password protecting streams.
It took me a while to figure out the streams, due to misleading Dahua style URL working somewhat. This will work rtsp://192.168.1.200:554/cam/realmonitor?channel=0&subtype=0 but it disregards the channel or subtype selection and only gives sub stream (“minor” in ILDVR terms). That URL is not correct.
Below are correct urls (I lifted them off the javascript in the webUI).
Main stream (aka “major”):
rtsp://192.168.1.200:554/1/h264majorSub stream (aka “minor”):
rtsp://192.168.1.200:554/1/h264minorSnapshot URL:
http://admin:admin@192.168.1.200/jpgimage/1/image.jpgNot sure what is the correct URL for mjpeg stream…
Interesting that the camera supports H265/HEVC. I am yet to test it (need to compile ffmpeg with h265 support).
The resolution selection goes all the way up to 2592×1944 (“2K”) on the “major” stream.
As typical there are stream errors with UDP stream (TCP stream is OK).
In general Web UI is very crappy and not tailored to the camera. It does not even get the camera model correctly.
There is a special clause in javascript for hi3518E chip (for whatever reason?).
I have spent a few hours pocking around the camera I noticed a few issues with webUI. I could crash (in a minor way) the camera with malformed fields when setting the time (via curl POST) as the validation happens in the javascript.
The smtp,ftp and alarm settings don’t work. The motion detect is useless without ftp/smtp or alarm settings.
The following quirks I found:
/form/, /cgi/ and /cgi-bin/ are all the same paths.
There is a “form” validation which does not allow arbitrary /cgi-bin/ script execution.
The simple path traversal exploit does not work.
Various little hack failed (command execution, remote inclusion, etc.), but I haven’t tried hard enough (I don’t normally hack things).
Any URL ending with image.jpg will result of attempting to get a snapshot from camera.
The ones that dont match jpgimage/1/image.jpg result in following output:
HTTP/1.0 200 OK
Content-Type: text/html
Image error
This potentially could be exploited (I don’t know how yet).
A lot of validation is happening in javascript. It is possible to set IP address, create username or almost any other field to any test string. I am currently trying to exploit this “feature”.
There are also a few places in javascript that has hard-coded “admin/admin” username and password:
document.getElementById("replay").SetLoginParam(srcIP,'admin','admin'); //justin changed 2013.6.27
document.getElementById("replay").SetLoginParamEx(srcIP,'admin','admin',$("#httpPort").val(),$("#rtspPort").val()); //2014.04.12and:
player.RunPlayEx(ipAddr.toString(),0,"0.0.0.0",2,90,0,"admin","admin");
There are a lot of references to “justin” all over the place.
The onvif located at http://192.168.1.200:8999/onvif/
The onvif is not password protected!!!! (I can add remove users, reboot camera, change passwords, etc).
The server headers are very similar to Hikvision (only it is “Hankvision”, lol WTF?):
HTTP/1.1 200 Data follows
Server: Hankvision-Webs
Date: Thu Dec 24 12:44:27 2015
Pragma: no-cache
Cache-Control: no-cache
Content-Type: text/html
Digging more around I found that OMEGA-21P22-12 has same firmware (I googled the firmware version number out of desperation).
Basically I am thinking of getting serial port hooked up the board as the manufacturer is silent regarding telnet/shell access and I do not trust this firmware at all.
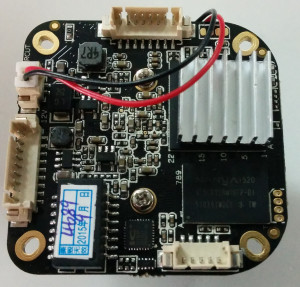
Here are the innards (the simplest way to remove the board is to unclip IR cover from front using two clips on the side):
SoC board (unfortunately cannot tell the model of SoC due to heatsink, looks like Hisilicon, possibly Hi3516D):
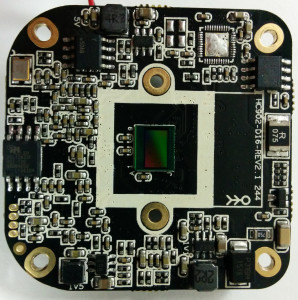
Sensor (I assume it is OV4689):
Conclusion.
It started all promising (communication, pricing and delivery). Hardware is great. Firmware is the show stopper.
I am thinking of putting off buying ILDVR cameras due to “secrecy” regarding firmware and telnet access (not unless I can flash them with generic Hivision firmware).
I’ll probably stick to Dahua, as at least I have shell access on those (and I can hack firmware to fix/address whatever issues arise). Even though Dahua does not want to deal with me directly…
Update: I managed to get shell on it, more info here.









Hello looks like Hankvision company is now actually hosting files including Firmware and SDK,
https://translate.google.com/translate?prev=_t&hl=en&ie=UTF-8&u=http://www.hankvision.com/NewsStd.html&sl=auto&tl=en